Twenty of Australia's ASX top 200 organisations are exposed to the dangerous 'heartbleed' vulnerability in OpenSSL revealed this week.
OpenSSL, an open-source implementation of the SSL and TLS protocols, contains a bug in its heartbeat extension that validates site connections.
Attackers could exploit the read-overrun bug to quietly connect to vulnerable servers, which would leak memory that could include usernames and passwords and even the SSL server's private key.
Those with access to the key could use it to impersonate a site even after the bug has been fixed, and likely crawl over and decrypt encrypted data. Man in the middle attacks could be performed by those with private keys in hand.
Scores of insecure sites have been detected and some of the biggest websites including Amazon and Wordpress have rushed to apply a patch for the two-year old vulnerability.
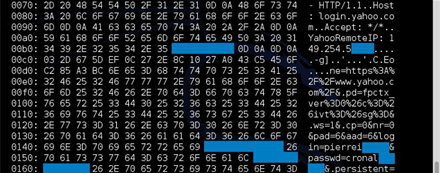
Yahoo! has also plugged the hole, but failed to act on early advice from Google and Codenomicon researchers who tipped off some sites ahead of this week's disclosure. That led to the exposure of usernames and passwords for users of its email service.
Statistics from metrics company Netcraft show that 66 percent of websites run open source web servers Apache and nginx, which use OpenSSL as the default encryption system.
HackLabs director Chris Gatford ran quick tests of the top 200 organisations listed on the Australian Stock Exchange and found 20 which were still exposed.
He said applying the fix would be painful for some organisations but necessary, as attackers may target the bug for a long time.
Scores more sites have been found to be vulnerable by researchers and attackers by using simple scripts and online tools.
Security researchers have also posted proof of concept scripts to find and hijack user sessions from vulnerable servers en masse.
But Google researcher Neel Mehta, who helped discover the bug, said exposure of private keys was unlikely due to memory allocation patterns.
Heap allocation patterns make private key exposure unlikely for #heartbleed #dontpanic.
— Neel Mehta (@neelmehta) April 8, 2014
While it remained critical that organisations apply the OpenSSL patch, doing so mitigated only one part of the threat.
Web administrators concerned that their website was exploited in the two years the bug existed under the radar should obtain new digital certificates.
Those admins worried that attackers have gained access to private keys should join the few to deploy Perfect Forward Secrecy, a powerful tool to prevent attackers from decrypting data sent during the past two years.
Security boffins also advise that passwords should be changed, a step that some websites are already taking.
Organisations running the Snort security software should review a list of signatures for the platform which will detect successful attacks against heartbleed.